
Steganography is the art or practice of concealing a message, image, or file within another message, image, or file. CTF steganography usually involves finding the hints or flags that have been hidden with steganography (most commonly a media file). A rudimentary knowledge of media filetypes (e.g. jpg, bmp, png for pictures and wav, mp3 for sound) is essential to steganography, as understanding in what ways files can be hidden and obscured is crucial. Also, understanding basic Linux is important, as a multitude of tools run in the Linux shell.
Steganography Concepts/Techniques
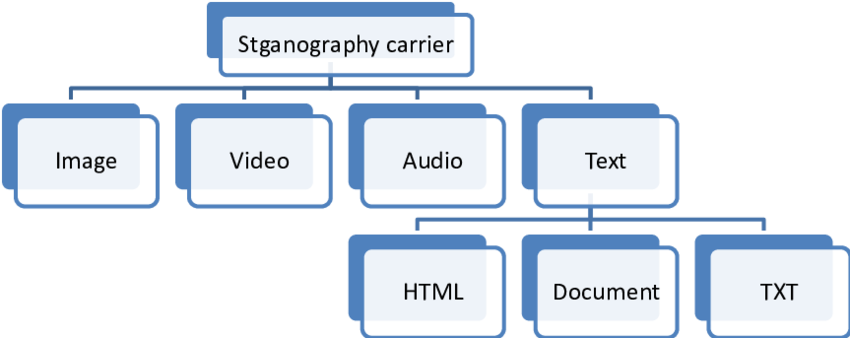
Depending on the nature of the cover object (actual object in which secret data is embedded), steganography can be divided into five types (see below). Most competitions will focus on image file challenges:
- Text Steganography
- Image Steganography
- Video Steganography
- Audio Steganography
- Network Steganography
Example Decoding Steps
Image file steps:
- Determine if you are trying to view embedded text or extract a hidden file.
- Try Web based tools:
- Try viewing with Online Stegnographic Decoder.
- Try changing bit plane using viewer like GeorgeOM.net (especially for images with only one visible color).
- Try viewing with Online Stegnographic Decoder.
- Try opening the file in a Hex Editor and look for imbedded text
- Try using the Digital Invisible Ink Toolkit to find imbedded pictures
- Try Linux Tools:
- Review the filename or extension for hints
- Try running the ‘$ file [filename]‘ to get more info on the file type.
- Try running the ‘$ strings [filename]‘ command for text
- Try running the ‘$ binwalk -e [filename]‘ to extract hidden files
- Try using Steghide or Stegosuite in linux (‘$ sudo apt-get install steghide‘ or ‘$ sudo apt-get install stegosuite‘
- Refer to the ‘Basic Linux Commands‘ page for more info on commands
Audio File – Decoding Steps:
- Step 1: Try online web-based tools:
- Try extracting with Online Stegnographic Decoder.
- Step 2: Use basic commands to confirm file type, extract meta data and find hints:
- file -> confirm file type (e.g, file audio.wav )
- exiftool -> extract meta data (e.g., exiftool audio.wav)
- strings -> look for comments (e.g., strings audio.wav | awk ‘length($0)>8’ )
- mediaInfo -> extract meta ;same as exiftool ; use one or another (e.g., mediainfo audio.wav )
- binwalk-> look for embedded files (e.g., ‘binwalk‘ command to extract embedded files and executables
- hexdump -> look for corruption (tbd)
- Step 3 : Use known Sound Visualization Tools (e.g, Sonic Visualisier)
- analyze freq spectrums and waveform for a hidden text/flag by tweaking around the brightness/contrast, etc.
- Step 4: Least-significant-bits (LSB) analyzing or secret txt
- hexdump -> look for LSB that is hiding text (tbd – advanced ?)
Refer to the ‘Basic Linux Commands‘ page for more info on commands
Steganography Tools:
- StegOnline – web-based, enhanced and open-source port of StegSolve.
- Stegnographic Decoder – Web based tool decodes payload hidden in a JPEG, WAV, or AU audio file using the encoder
- Hex Editor – browser based hex editor
- ‘strings‘ command to view visible text characters
- ‘binwalk‘ command to extract embedded files and executable code
- Digital Invisible Ink Toolkit – Use algorythms to decode
- Steghide – open source steganography software (Linux)
- Stegosuite – a free steganography tool written in Java (Linux).
- pngcheck – look for/correct broken chunks. Run pngcheck -vtp7f filename.png to view all info.
- GeorgeOM.net – Geo Explore Colour & Bit Planes (Go to “Browse Bit Planes”) … Used in many white page exercises .
References:
- Steganography Tutorial – A Complete Guide For Beginners by Archana Choudary
- Steganography in Kali Linux – Hiding data in image by Vijay Kumar
- How To Use Steghide And StegoSuite Steganography Tools In Kali Linux
- Stegnography Cheet Sheet
- Get Secret Message from an Audio file